Today I was trying to find a list of all attributes synchronized to Office365 by DirSync. I couldn’t find a published list so I figured I’d just get it from the MA, using powershell to extract the list of source attributes. The list of AD user attributes synchronized by DirSync is at the bottom of this post, and in between I’ll show you how I got there.
Note while I’m talking DirSync here this method will work for MIIS, ILM and FIM Management Agents.
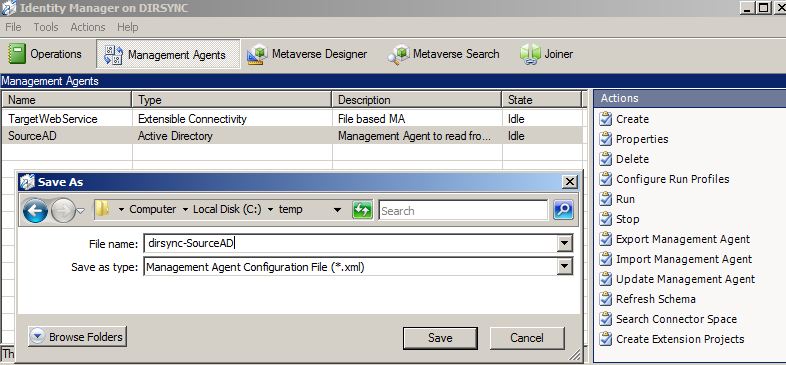
Export the MA
DirSync is just ILM and you can get into the Identity Manager client by running:
C:\Program Files\Microsoft Online Directory Sync\SYNCBUS\UIShell\miisclient.exe
Note: If you get an error about not having rights then add your account into the MIISAdmins group on the DirSync server then re-login.
Open the “Management Agents” page, click on the “SourceAD” MA to highlight it, then choose “Export Management Agent” from the Actions menu., and save the XML file.
Parse the XML file in Powershell
Now I go into powershell and load the content of the xml file into a variable:
PS C:\scripts> [xml]$xml = get-content .\dirsync-sourceAD.xml
I can see all the import attribute flows like this:
PS C:\scripts> $xml."export-ma"."mv-data"."import-attribute-flow"."import-flow-set"
mv-object-type import-flows
-------------- ------------
group {import-flows, import-flows, import-flows, import-flows...}
contact {import-flows, import-flows, import-flows, import-flows...}
person {import-flows, import-flows, import-flows, import-flows...}
Right now I’m only interested in the “person” attribute flows:
PS C:\scripts> $xml."export-ma"."mv-data"."import-attribute-flow"."import-flow-set"[2]
mv-object-type import-flows
-------------- ------------
person {import-flows, import-flows, import-flows, import-flows...}
This next one lists the defined attribute flows. There’s a lot more but I’m just showing the top few.
PS C:\scripts> $xml."export-ma"."mv-data"."import-attribute-flow"."import-flow-set"[2]."import-flows"
mv-attribute type import-flow
------------ ---- -----------
assistant ranked {import-flow, import-flow}
company ranked {import-flow, import-flow}
department ranked {import-flow, import-flow}
displayName ranked {import-flow, import-flow}
facsimileTelephoneNumber ranked {import-flow, import-flow}
givenName ranked {import-flow, import-flow}
It might look as though the mv-attribute is what I want, but actually that’s an internal sync service attribute, and not the Active Directory attribute. I need to go a little deeper into the xml to get that.
First I’ll define a new variable to simplify my xml path:
PS C:\scripts> $importflows = $xml."export-ma"."mv-data"."import-attribute-flow"."import-flow-set"[2]."import-flows"
Then all I have to do is loop through picking out the “src-attribute”. The results are listed below:
PS C:\scripts> foreach ($iaf in $importflows) {$iaf."import-flow"[0]."direct-mapping"."src-attribute"}
assistant
company
department
displayName
facsimileTelephoneNumber
givenName
homePhone
initials
manager
mobile
physicalDeliveryOfficeName
postalCode
telephoneNumber
title
mailNickname
ipPhone
middleName
otherFacsimileTelephoneNumber
otherHomePhone
otherIpPhone
otherMobile
otherPager
otherTelephone
pager
countryCode
description
info
streetAddress
wWWHomePage
url
extensionAttribute11
extensionAttribute12
extensionAttribute13
extensionAttribute14
extensionAttribute15
mail
cn
l
co
sn
st
postOfficeBox
msRTCSIP-UserEnabled
legacyExchangeDN
msExchHideFromAddressLists
msExchMailboxGuid
msExchAssistantName
msDS-HABSeniorityIndex
msDS-PhoneticDisplayName
msExchArchiveGUID
msExchBypassModerationFromDLMembersLink
msExchBypassModerationLink
msExchEnableModeration
msExchImmutableId
msExchModeratedByLink
msExchModerationFlags
msExchRecipientDisplayType
msExchResourceCapacity
preferredLanguage
publicDelegates
telephoneAssistant
msExchResourceDisplay
thumbnailPhoto
msExchBlockedSendersHash
msExchSafeRecipientsHash
msExchSafeSendersHash
extensionAttribute1
extensionAttribute10
extensionAttribute2
extensionAttribute3
extensionAttribute4
extensionAttribute5
extensionAttribute6
extensionAttribute7
extensionAttribute8
extensionAttribute9
msExchResourceMetaData
msExchResourceSearchProperties
msRTCSIP-Line
msRTCSIP-PrimaryUserAddress
targetAddress
msExchSenderHintTranslations
msExchArchiveName
msRTCSIP-DeploymentLocator
msExchRemoteRecipientType
msExchLitigationHoldDate
msExchLitigationHoldOwner
msExchRecipientTypeDetails
msExchRetentionComment
msExchRetentionURL
msExchAuditAdmin
msExchAuditDelegate
msExchAuditDelegateAdmin
msExchBypassAudit
msExchDelegateListLink
msExchELCExpirySuspensionEnd
msExchELCExpirySuspensionStart
msExchELCMailboxFlags
msExchMailboxAuditEnable
msExchMailboxAuditLogAgeLimit
msRTCSIP-OptionFlags
msExchUsageLocation
____________________________________________________________________________________________________________________________________________________________________________________
Great post Carol!
I’ve always hated having to wrap quotes around the elements and nodes due to the dash character so, feeling rather geeky, thought I’d share the System.Xml.XmlNode.SelectNodes approach. If you care, here’s the above as one line (assuming filePath is set to the location of the XML):
((Get-Content $filePath) -as [System.Xml.XmlDocument]).SelectNodes(“export-ma/mv-data/import-attribute-flow/import-flow-set[@mv-object-type = ‘person’]/import-flows/import-flow/direct-mapping/src-attribute”) | ft `#text -HideTableHeaders;
And here it is all nicely typed:
[System.Xml.XmlDocument]$exma = Get-Content $filePath;
[System.Xml.XmlNodeList]$dmSrcAttrs = $exma.SelectNodes(“export-ma/mv-data/import-attribute-flow/import-flow-set[@mv-object-type = ‘person’]/import-flows/import-flow/direct-mapping/src-attribute”);
$dmSrcAttrs | ft `#text -HideTableHeaders;
🙂
Thanks Paul – that does look neat!
Thanks Carol your Blog just got me out of a sticky situation.
Regards you old LBS padawan
Hi Steve! Glad to help 🙂
Hi Carol,
Thanks for sharing your expertise here. My organization would like to take advantage of Office 365 support of S/MIME encryption (i.e. user certificate). So far, we have been able to perform this manually via Outlook using the Publish to GAL mechanism to push certificates to the cloud-side directory. As of yet, we cannot find a supported method to perform this action via dirsync. Is it possible to make a modification to the ILM configuration to attempt to synchronize the userCertificate attribute? Or is it likely that the security will likely not permit this? Or perhaps some other scenario?
Thanks for your time,
Eli
You can’t change DirSync. Firstly it’s not supported, and secondly you can’t sync to an attribute that is not being expected by the receiver at the other end. It’s possible there’s a powershell way to do this – if not you will probably be reduced to bugging Microsoft to get it added.
Understood. This has been pursued with Microsoft and Office 365 does not consider this on its roadmap. Thanks for your time!
I’m wondering if there’s a way you can automate it on the client side – is this Publish to GAL function scriptable?
I researched this somewhat and concluded the following:
The “Publish to GAL” button is not exposed
Native macro (ugly) is not an option due to security updates that (appropriately) prevent menu navigation and send keys
I’m now faced with using the lowest form of automation: third-party scripting tool that navigates menus to the Publish to GAL and examines subsequent windows to workflow users through the process of manually pushing their certificates to the cloud directory. Inelegant, at best.
Thoughts?
Only thought, apart from “good luck with that”, is that it might be worth talking to MessageOps. They have some good workarounds for various management problems with Office365.
Cool. Thanks Carol for your consideration.
Eli
Here is the published list : http://support.microsoft.com/kb/2256198